BUUCTF刷题
[SUCTF2018]single dog
打开图片binwalk分析得到压缩包,得到一个文件,里面是一堆表情,发现是js加密(其实就是AAEncode加密)
在控制台粘贴代码,并删去最后一个表情得到

间谍启示录
分析光盘没有发现什么,strings 搜flag,得到flag.exe foremost得到,然后双击点开,得到 机密文件.txt

隐藏的项目打开还是挺好用的
小易的U盘
打开光盘文件,010查看文件头为rar文件,打开autorun.inf文件
大多数病毒在入侵U盘时,都会在U盘里创建一个autorun.inf文件,再把病毒路径植入到这个程序里,然后才开始搞破坏。
[AutoRun]
Open=autoflag - 副本 (32)‘
所以直接找该exe文件
然后strings 提取
strings q.exe |grep flag
flag{29a0vkrlek3eu10ue89yug9y4r0wdu10}
D:/Program/flag.txt
flag == 0 || flag == 1
F:\autoflag\Debug\autoflag.pdb[HDCTF2019]你能发现什么蛛丝马迹吗
volatility分析得到
分析cmd进程查看
/volatility -f memory.img --profile=Win2003SP1x86 cmdscan
Volatility Foundation Volatility Framework 2.6
**************************************************
CommandProcess: csrss.exe Pid: 516
CommandHistory: 0x398fba8 Application: DumpIt.exe Flags: Allocated
CommandCount: 0 LastAdded: -1 LastDisplayed: -1
FirstCommand: 0 CommandCountMax: 50
ProcessHandle: 0x6e4猜测DumpIt.exe有东西,dump下来
./volatility -f memory.img --profile=Win2003SP1x86 memdump -p 1992 -D ./
Volatility Foundation Volatility Framework 2.6
************************************************************************
Writing explorer.exe [ 1992] to 1992.dmp然后直接分离
得到


二维码得到 jfXvUoypb8p3zvmPks8kJ5Kt0vmEw0xUZyRGOicraY4=
由于有key 和 iv 所以直接AES解密 在线AES加密解密 - 拉米工具 (lmeee.com)

py解密
from Crypto.Cipher import AES
from Crypto.Util.Padding import pad, unpad
import base64
password = b'Th1s_1s_K3y00000' #秘钥,b就是表示为bytes类型
text = b'jfXvUoypb8p3zvmPks8kJxjg3seW76u5hYVke4vgLbg=' #需要解密的密文,bytes类型
aes = AES.new(password, AES.MODE_ECB) #创建一个aes对象
# AES.MODE_ECB 表示模式是ECB模式
# 先将 base64 编码的密文解码为 bytes 类型
text = base64.b64decode(text)
decrypted_text = aes.decrypt(text) # 解密密文
# 使用 PKCS7 方式解除填充
unpadded_text = unpad(decrypted_text, AES.block_size)
print("明文:", unpadded_text.decode('utf-8')) #解密后的明文USB
给了一个rar文件和key.ftm
rar文件放入010中提示了
header crc mismatch in block #3
CTF解题技能之压缩包分析基础篇 - FreeBuf网络安全行业门户
分析压缩文件的格式发现,233.png文件块的标识出现错误,需将7A改为74,然后就可以解压文件,得到了一张图片,在stegsolve中的blue0通道中发现一张二维码。解码得到ci{v3erf_0tygidv2_fc0}。
然后分析key文件,直接binwalk分离,得到一个压缩包,里面有一个流量包,由于时usb流量,直接tshark分离,发现是8字节,直接键盘流量解密。得到
[+] Found : aababacbbdbdccccdcdcdbbcccbcbbcbbaababaaaaaaaaaaaaaaaaaakey{xinan}
应该是维吉尼亚密码,直接解开,然后是栅栏密码。

[GUET-CTF2019]zips
打开压缩包,得到一个新的压缩包。查看文件头,发现是真加密,暴力破解得到 “723456”.
然后得到111.zip,里面有一个加密文件,是伪加密,解开后得到

steup.sh打开后
#!/bin/bash
\#
zip -e --password=`python -c "print(__import__('time').time())"` flag.zip flag知道密码为python当时的时间戳,由于是2019年的题,所以搜了一下,当时的时间戳应该是15开头。
而flag.zip又有密码,因此掩码爆破得到flag

[DDCTF2018]流量分析
提示一:若感觉在中间某个容易出错的步骤,若有需要检验是否正确时,可以比较MD5: 90c490781f9c320cd1ba671fcb112d1c
提示二:注意补齐私钥格式
打开流量包后发现有tls流量。
那就wireshark打开,筛选tcp contains “KEY”
发现有许多的base串
解码后发现是一张PNG格式的图片


将其复制下来,在进行对照,并补全密钥。
-----BEGIN RSA PRIVATE KEY-----
MIICXAIBAAKBgQDCm6vZmclJrVH1AAyGuCuSSZ8O+mIQiOUQCvN0HYbj8153JfSQ
LsJIhbRYS7+zZ1oXvPemWQDv/u/tzegt58q4ciNmcVnq1uKiygc6QOtvT7oiSTyO
vMX/q5iE2iClYUIHZEKX3BjjNDxrYvLQzPyGD1EY2DZIO6T45FNKYC2VDwIDAQAB
AoGAbtWUKUkx37lLfRq7B5sqjZVKdpBZe4tL0jg6cX5Djd3Uhk1inR9UXVNw4/y4
QGfzYqOn8+Cq7QSoBysHOeXSiPztW2cL09ktPgSlfTQyN6ELNGuiUOYnaTWYZpp/
QbRcZ/eHBulVQLlk5M6RVs9BLI9X08RAl7EcwumiRfWas6kCQQDvqC0dxl2wIjwN
czILcoWLig2c2u71Nev9DrWjWHU8eHDuzCJWvOUAHIrkexddWEK2VHd+F13GBCOQ
ZCM4prBjAkEAz+ENahsEjBE4+7H1HdIaw0+goe/45d6A2ewO/lYH6dDZTAzTW9z9
kzV8uz+Mmo5163/JtvwYQcKF39DJGGtqZQJBAKa18XR16fQ9TFL64EQwTQ+tYBzN
+04eTWQCmH3haeQ/0Cd9XyHBUveJ42Be8/jeDcIx7dGLxZKajHbEAfBFnAsCQGq1
AnbJ4Z6opJCGu+UP2c8SC8m0bhZJDelPRC8IKE28eB6SotgP61ZqaVmQ+HLJ1/wH
/5pfc3AmEyRdfyx6zwUCQCAH4SLJv/kprRz1a1gx8FR5tj4NeHEFFNEgq1gmiwmH
2STT5qZWzQFz8NRe+/otNOHBR2Xk4e8IS+ehIJ3TvyE=
-----END RSA PRIVATE KEY-----
在导入tsl密钥,过滤http,即可得到flag
[b01lers2020]image_adjustments

就是把所有红线全放到上面或者下面,然后使得黑线跟着移动,最终得到flag。
from PIL import Image
def re_turn(pixels,num):
return pixels[num:]+pixels[:num]
p = Image.open('attachment.png').convert('RGB')
a,b = p.size
pixels=[]
for x in range(a):
pixel = []
for y in range(b):
pixel.append(p.getpixel((x,y)))
pixels.append(pixel)
data = []
for i in pixels:
for j in range(len(i)):
if i[j] != i[j-1] and i [j-1] == (255,0,0):
data.append(j)
break
_pixels = []
for i in range(len(data)):
_pixels.append(re_turn(pixels[i],data[i]))
p1 = Image.new('RGB',(a,b))
for x in range(a) :
for y in range(b):
p1.putpixel((x,y),_pixels[x][y])
p1.save('flag1.png')
洞拐洞拐洞洞拐

该图有许多黑白像素
from PIL import Image
MAX = 320
p =Image.open('2.png').convert('L')
fp = open('2.txt','w')
flag = ''
for x in range(MAX):
for y in range(MAX):
if p.getpixel((x,y))==255:
flag += '0'
if p.getpixel((x,y))== 0 :
flag += '1'
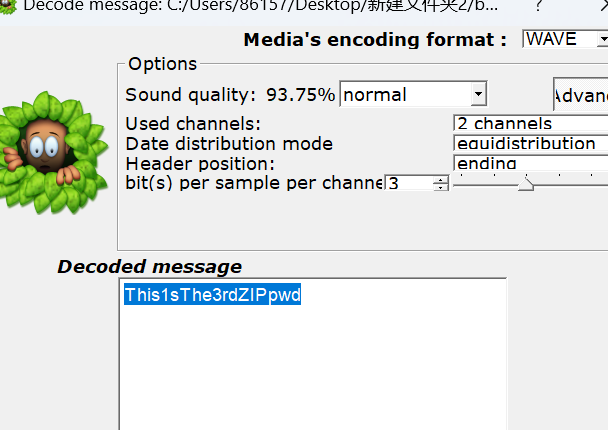
fp.write(flag)在转二进制后,发现是一个wav文件,保存下来,打开

发现每秒有十帧,共有八种不同的高度
import wave
import base64
f = wave.open("2.wav","rb")
params=f.getparams()
nchannels, sampwidth, framerate, nframes = params[:4]
flag = ''
rflag = ''
for i in range(319):
strData=f.readframes(10)
if strData == b'\x01\xa0\x01\xa0\x01\xa0\x01\xa0\x01\xa0\x01\xa0\x01\xa0\x01\xa0\x01\xa0\x01\xa0':
flag += '0'
if strData == b'\x01\xc0\x01\xc0\x01\xc0\x01\xc0\x01\xc0\x01\xc0\x01\xc0\x01\xc0\x01\xc0\x01\xc0':
flag += '1'
if strData == b'\x01\xe0\x01\xe0\x01\xe0\x01\xe0\x01\xe0\x01\xe0\x01\xe0\x01\xe0\x01\xe0\x01\xe0':
flag += '2'
if strData == b'\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00':
flag += '3'
if strData == b'\xff\x1f\xff\x1f\xff\x1f\xff\x1f\xff\x1f\xff\x1f\xff\x1f\xff\x1f\xff\x1f\xff\x1f':
flag += '4'
if strData == b'\xff?\xff?\xff?\xff?\xff?\xff?\xff?\xff?\xff?\xff?':
flag += '5'
if strData == b'\xff_\xff_\xff_\xff_\xff_\xff_\xff_\xff_\xff_\xff_':
flag += '6'
if strData == b'\xff\x7f\xff\x7f\xff\x7f\xff\x7f\xff\x7f\xff\x7f\xff\x7f\xff\x7f\xff\x7f\xff\x7f':
flag += '7'
flag += '5'
for i in range(0,len(flag),3):
b = flag[i]+flag[i+1]+flag[i+2]
c = int(b,8)
rflag += chr(c)
rflag += '======'
flag = base64.b32decode(rflag)
print(flag)[SUCTF2019]protocol
USB流量导出
tshark -r 1.pcapng -T fields -e usb.capdata | sed '/^\s*$/d' > usbdata.txt什么都没有发现,然后检查流量包发现png
foremost分离得到

发现十五个字母图片后面有是个黑色图片,继续看流量包

发现数据第三个比特有规律变化,前十五个为图片顺序后面使黑色的顺序,对应得到
04 03 02 01 00 09 08 07 06 05 0e 0d 0c 0b 0a
06 07 0e 04 01 0d 00 02 0b 09
04 03 02 01 00 09 08 07 06 05 0e 0d 0c 0b 0a
01 0e 08 06 0d 0c 00 05 09 0b
04 03 02 01 00 09 08 07 06 05 0e 0d 0c 0b 0a
02 09 03 05 01 07 0d 0b 0e 04
04 03 02 01 00 09 08 07 06 05 0e 0d 0c 0b 0a
06 0d 0a 08 09 04 0b 03 0c 02
04 03 02 01 00 09 08 07 06 05 0e 0d 0c 0b 0a
# 将重复多余的删除就是得到
04 03 02 01 00 09 08 07 06 05 0e 0d 0c 0b 0a
06 07 0e 04 01 0d 00 02 0b 09
01 0e 08 06 0d 0c 00 05 09 0b
02 09 03 05 01 07 0d 0b 0e 04
06 0d 0a 08 09 04 0b 03 0c 02
suctf{My_usb_pr0toco1_s0_w3ak}
[MRCTF2020]千层套路
题目是一个压缩包套娃,密码是该文件的名字
import zipfile
import os
name = '0573'
while True:
r = zipfile.ZipFile(name+'.zip','r')
r.extractall(path='.',pwd=bytes(name,'utf-8'))
r.close()
os.remove(name+'.zip')
name = r.namelist()[0][0:4]
得到qr.zip,打开后发现应该是一个图片
(255, 255, 255)
(255, 255, 255)
(255, 255, 255)
(255, 255, 255)
(255, 255, 255)
(255, 255, 255)
(255, 255, 255)
(255, 255, 255)
(255, 255, 255)
(255, 255, 255)
(255, 255, 255)python得到
from PIL import Image
from zlib import*
file = open('qr.txt','r')
i=0
pic = Image.new("RGB",(200,200))
for y in range(200):
for x in range(200):
color=file.readline()
pic.putpixel([x,y],eval(color)) #eval函数可以直接得到元组
pic.save('1.png')
发现是一个二维码,解码得到flag
一路到底
题目给了许多txt文件。
最下面有一个start.txt,打开发现
20555 : The next is a8242a234560a0d3cf121864ee34d7fb.txt前面数字hex转化后未504B,下一个则是0304,猜测是一个压缩包。
import binascii
from tqdm import tqdm
flag = ''
with open ('start.txt') as f:
text = f.read()
nexxt = text[-36:]
data='{:04x}'.format(int(text[0:text.find(':')-1]))
print(type(data))
flag += data
print(text, '\t', nexxt, '\t', data)
for i in tqdm(range(160000)):
try:
with open(nexxt) as f:
text = f.read()
nexxt = text[-36:]
data = '{:04x}'.format(int(text[0:text.find(':')-1]))
flag += data
except:
print(flag)
break
with open('123.zip', 'wb') as dw:
dw.write(binascii.unhexlify(flag))然后破解密码。
得到一个png,其实是jpg格式,修改得到图片。

key不在这里
给了一个二维码,解码得到
https://cn.bing.com/search?q=key%E4%B8%8D%E5%9C%A8%E8%BF%99%E9%87%8C&m=10210897103375566531005253102975053545155505050521025256555254995410298561015151985150375568&qs=n&form=QBRE&sp=-1&sc=0-38&sk=&cvid=2CE15329C18147CBA4C1CA97C8E1BB8C发现中间有一串数字
10210897103375566531005253102975053545155505050521025256555254995410298561015151985150375568猜测是ascii码
import urllib.parse
s = '10210897103375566531005253102975053545155505050521025256555254995410298561015151985150375568'
tem = ''
while len(s):
if int(s[:3])<127:
tem += chr(int(s[:3]))
s = s[3:]
else:
tem +=chr(int(s[:2]))
s= s[2:]
# print(tem) flag%7B5d45fa256372224f48746c6fb8e33b32%7D
url = urllib.parse.unquote(tem)
print(url) # flag{5d45fa256372224f48746c6fb8e33b32}[DDCTF2018]第四扩展FS
binwalk分析图片得到压缩包,再exif找到提示,打开压缩包,得到

看提示是词频分析
from collections import Counter
with open('file.txt','r')as f:
s=f.read()
result = Counter(s)
#print(result)
flag=[key for key , value in sorted(result.items(),key=lambda k:k[1],reverse =True )]
print(''.join(flag)) # DCTF{huanwe1sik4o!}[*CTF2019]babyflash
一个flash文件利用 jpexi进行分离得到 一个wav文件和一堆二维码部分
二维码进行组装
from PIL import Image
def aaa(s):
image = Image.open("frames/"+str(i)+".png")
a,b,c,d = image.getpixel((50,50))
return a
data=''
for i in range(1,442):
if aaa(i)==0:
data+='1'
else:
data+='0'
length = 21
img = Image.new('RGB', (length * 5, length * 5))
for x in range(length):
for y in range(length):
if data[x*length+y] == '1':
for xx in range(x*5, x*5+5):
for yy in range(y*5, y*5+5):
img.putpixel([xx, yy], (0, 0, 0))
else:
for xx in range(x*5, x*5+5):
for yy in range(y*5, y*5+5):
img.putpixel([xx, yy], (255, 255, 255))
# 保存新图像
img.save('flag.png')
wav解开后得到flag
*ctf{half_flag_&&_the_rest}[羊城杯 2020]逃离东南亚
打开是三个压缩包,第一个没有密码,给了一个png图片,发现宽高有问题
import os
import binascii
import struct
crcbp = open("img.png", "rb").read()
original_crc32 = int(crcbp[29:33].hex(), 16)#打开图片
for i in range(2000):
for j in range(2000):
data = crcbp[12:16] + \
struct.pack('>i', i)+struct.pack('>i', j)+crcbp[24:29]
crc32 = binascii.crc32(data) & 0xffffffff
if(crc32 == original_crc32): #图片当前CRC
print(i, j)
print('hex:', hex(i), hex(j))
# 249 300 hex: 0xf9 0x12c修改后得到下一个压缩包的密码

明显是brainfuck,但是解密得到乱码失败。猜测解压后应该得到字符串,但是字符串brainfuck加密后应该是++++++++[开头的,与密文不符,尝试在开头加上++++++++后解密成功

elf文件打开
import base64
data = base64.b64decode('f0VMRgIBAQAAAAAAAAAAAAIAPgABAAAAcARAAAAAAABAAAAAAAAAAJgaAAAAAAAAAAAAAEAAOAAJAEAAHwAcAAYAAAAFAAAAQAAAAAAAAABAAEAAAAAAAEAAQAAAAAAA+AEAAAAAAAD4AQAAAAAAAAgAAAAAAAAAAwAAAAQAAAA4AgAAAAAAADgCQAAAAAAAOAJAAAAAAAAcAAAAAAAAABwAAAAAAAAAAQAAAAAAAAABAAAABQAAAAAAAAAAAAAAAABAAAAAAAAAAEAAAAAAAPwHAAAAAAAA/AcAAAAAAAAAACAAAAAAAAEAAAAGAAAAEA4AAAAAAAAQDmAAAAAAABAOYAAAAAAAnQIAAAAAAACgAgAAAAAAAAAAIAAAAAAAAgAAAAYAAAAoDgAAAAAAACgOYAAAAAAAKA5gAAAAAADQAQAAAAAAANABAAAAAAAACAAAAAAAAAAEAAAABAAAAFQCAAAAAAAAVAJAAAAAAABUAkAAAAAAAEQAAAAAAAAARAAAAAAAAAAEAAAAAAAAAFDldGQEAAAA1AYAAAAAAADUBkAAAAAAANQGQAAAAAAANAAAAAAAAAA0AAAAAAAAAAQAAAAAAAAAUeV0ZAYAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAEAAAAAAAAABS5XRkBAAAABAOAAAAAAAAEA5gAAAAAAAQDmAAAAAAAPABAAAAAAAA8AEAAAAAAAABAAAAAAAAAC9saWI2NC9sZC1saW51eC14ODYtNjQuc28uMgAEAAAAEAAAAAEAAABHTlUAAAAAAAIAAAAGAAAAIAAAAAQAAAAUAAAAAwAAAEdOVQBKGyxVsNKciPJwGAmlVuV44jwRVgEAAAABAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAACwAAABIAAAAAAAAAAAAAAAAAAAAAAAAAFgAAABIAAAAAAAAAAAAAAAAAAAAAAAAAKAAAACAAAAAAAAAAAAAAAAAAAAAAAAAAEAAAABIAAAAAAAAAAAAAAAAAAAAAAAAAAGxpYmMuc28uNgBwdXRzAHNsZWVwAF9fbGliY19zdGFydF9tYWluAF9fZ21vbl9zdGFydF9fAEdMSUJDXzIuMi41AAAAAAIAAgAAAAIAAAABAAEAAQAAABAAAAAAAAAAdRppCQAAAgA3AAAAAAAAAPgPYAAAAAAABgAAAAMAAAAAAAAAAAAAABgQYAAAAAAABwAAAAEAAAAAAAAAAAAAACAQYAAAAAAABwAAAAIAAAAAAAAAAAAAACgQYAAAAAAABwAAAAQAAAAAAAAAAAAAAEiD7AhIiwXtCyAASIXAdAXoSwAAAEiDxAjDAAAAAAAA/zXiCyAA/yXkCyAADx9AAP8l4gsgAGgAAAAA6eD/////JdoLIABoAQAAAOnQ/////yXSCyAAaAIAAADpwP////8lkgsgAGaQAAAAAAAAAAAx7UmJ0V5IieJIg+TwUFRJx8BQBkAASMfB4AVAAEjHx2YFQADop/////RmDx9EAAC4txBgAFVILbAQYABIg/gOSInldhu4AAAAAEiFwHQRXb+wEGAA/+BmDx+EAAAAAABdww8fQABmLg8fhAAAAAAAvrAQYABVSIHusBBgAEjB/gNIieVIifBIweg/SAHGSNH+dBW4AAAAAEiFwHQLXb+wEGAA/+APHwBdw2YPH0QAAIA9hgsgAAB1EVVIieXobv///13GBXMLIAAB88MPH0AAvyAOYABIgz8AdQXrkw8fALgAAAAASIXAdPFVSInl/9Bd6Xr///9VSInlSIPsEIl9/EiJdfC/aAZAAOix/v//vwEAAAC4AAAAAOjC/v//v3wGQADomP7//78BAAAAuAAAAADoqf7//7+KBkAA6H/+//+/AQAAALgAAAAA6JD+//+/qAZAAOhm/v//uAAAAADJw2YuDx+EAAAAAAAPH0QAAEFXQVZBif9BVUFUTI0lHgggAFVIjS0eCCAAU0mJ9kmJ1Uwp5UiD7AhIwf0D6O/9//9Ihe10IDHbDx+EAAAAAABMiepMifZEif9B/xTcSIPDAUg563XqSIPECFtdQVxBXUFeQV/DkGYuDx+EAAAAAADzwwAASIPsCEiDxAjDAAAAAQACAAAAAABoZWl+d2hhdCB5b3Ugd2FudD8/AHdhbnQgYSBmbGFnPyAAc29ycnl+dGhlcmUgaXMgbm8gZmxhZwAAAAAAAAAAYnV0IG1heWJlIHlvdXIgY2FuIGZpbmQgc29tZXRoaW5nIHVzZWZ1bCEAAAABGwM7MAAAAAUAAABM/f//fAAAAJz9//9MAAAAkv7//6QAAAAM////xAAAAHz///8MAQAAFAAAAAAAAAABelIAAXgQARsMBwiQAQcQFAAAABwAAABI/f//KgAAAAAAAAAAAAAAFAAAAAAAAAABelIAAXgQARsMBwiQAQAAJAAAABwAAADI/P//QAAAAAAOEEYOGEoPC3cIgAA/GjsqMyQiAAAAABwAAABEAAAA5v3//2sAAAAAQQ4QhgJDDQYCZgwHCAAARAAAAGQAAABA/v//ZQAAAABCDhCPAkIOGI4DRQ4gjQRCDiiMBUgOMIYGSA44gwdNDkByDjhBDjBBDihCDiBCDhhCDhBCDggAFAAAAKwAAABo/v//AgAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAQAVAAAAAAAAgBUAAAAAAAAAAAAAAAAAAAQAAAAAAAAABAAAAAAAAAAwAAAAAAAAAAARAAAAAAAANAAAAAAAAAFQGQAAAAAAAGQAAAAAAAAAQDmAAAAAAABsAAAAAAAAACAAAAAAAAAAaAAAAAAAAABgOYAAAAAAAHAAAAAAAAAAIAAAAAAAAAPX+/28AAAAAmAJAAAAAAAAFAAAAAAAAADADQAAAAAAABgAAAAAAAAC4AkAAAAAAAAoAAAAAAAAAQwAAAAAAAAALAAAAAAAAABgAAAAAAAAAFQAAAAAAAAAAAAAAAAAAAAMAAAAAAAAAABBgAAAAAAACAAAAAAAAAEgAAAAAAAAAFAAAAAAAAAAHAAAAAAAAABcAAAAAAAAAuANAAAAAAAAHAAAAAAAAAKADQAAAAAAACAAAAAAAAAAYAAAAAAAAAAkAAAAAAAAAGAAAAAAAAAD+//9vAAAAAIADQAAAAAAA////bwAAAAABAAAAAAAAAPD//28AAAAAdANAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAACgOYAAAAAAAAAAAAAAAAAAAAAAAAAAAADYEQAAAAAAARgRAAAAAAABWBEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGlzIHRoZXJlIGFueXRoaW5nPwAA5LmfAOiuuADkvaAA6K+lAOS6hgDop6MA5LiAAOS4iwDogIEA5rapAOmAvADpmpAA5YaZAAAAAAAAR0NDOiAoVWJ1bnR1IDUuNC4wLTZ1YnVudHUxfjE2LjA0LjEwKSA1LjQuMCAyMDE2MDYwOQAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAwABADgCQAAAAAAAAAAAAAAAAAAAAAAAAwACAFQCQAAAAAAAAAAAAAAAAAAAAAAAAwADAHQCQAAAAAAAAAAAAAAAAAAAAAAAAwAEAJgCQAAAAAAAAAAAAAAAAAAAAAAAAwAFALgCQAAAAAAAAAAAAAAAAAAAAAAAAwAGADADQAAAAAAAAAAAAAAAAAAAAAAAAwAHAHQDQAAAAAAAAAAAAAAAAAAAAAAAAwAIAIADQAAAAAAAAAAAAAAAAAAAAAAAAwAJAKADQAAAAAAAAAAAAAAAAAAAAAAAAwAKALgDQAAAAAAAAAAAAAAAAAAAAAAAAwALAAAEQAAAAAAAAAAAAAAAAAAAAAAAAwAMACAEQAAAAAAAAAAAAAAAAAAAAAAAAwANAGAEQAAAAAAAAAAAAAAAAAAAAAAAAwAOAHAEQAAAAAAAAAAAAAAAAAAAAAAAAwAPAFQGQAAAAAAAAAAAAAAAAAAAAAAAAwAQAGAGQAAAAAAAAAAAAAAAAAAAAAAAAwARANQGQAAAAAAAAAAAAAAAAAAAAAAAAwASAAgHQAAAAAAAAAAAAAAAAAAAAAAAAwATABAOYAAAAAAAAAAAAAAAAAAAAAAAAwAUABgOYAAAAAAAAAAAAAAAAAAAAAAAAwAVACAOYAAAAAAAAAAAAAAAAAAAAAAAAwAWACgOYAAAAAAAAAAAAAAAAAAAAAAAAwAXAPgPYAAAAAAAAAAAAAAAAAAAAAAAAwAYAAAQYAAAAAAAAAAAAAAAAAAAAAAAAwAZAEAQYAAAAAAAAAAAAAAAAAAAAAAAAwAaAK0QYAAAAAAAAAAAAAAAAAAAAAAAAwAbAAAAAAAAAAAAAAAAAAAAAAABAAAABADx/wAAAAAAAAAAAAAAAAAAAAAMAAAAAQAVACAOYAAAAAAAAAAAAAAAAAAZAAAAAgAOAKAEQAAAAAAAAAAAAAAAAAAbAAAAAgAOAOAEQAAAAAAAAAAAAAAAAAAuAAAAAgAOACAFQAAAAAAAAAAAAAAAAABEAAAAAQAaAK0QYAAAAAAAAQAAAAAAAABTAAAAAQAUABgOYAAAAAAAAAAAAAAAAAB6AAAAAgAOAEAFQAAAAAAAAAAAAAAAAACGAAAAAQATABAOYAAAAAAAAAAAAAAAAAClAAAABADx/wAAAAAAAAAAAAAAAAAAAACsAAAAAQAZAGAQYAAAAAAATQAAAAAAAAABAAAABADx/wAAAAAAAAAAAAAAAAAAAACyAAAAAQASAPgHQAAAAAAAAAAAAAAAAADAAAAAAQAVACAOYAAAAAAAAAAAAAAAAAAAAAAABADx/wAAAAAAAAAAAAAAAAAAAADMAAAAAAATABgOYAAAAAAAAAAAAAAAAADdAAAAAQAWACgOYAAAAAAAAAAAAAAAAADmAAAAAAATABAOYAAAAAAAAAAAAAAAAAD5AAAAAAARANQGQAAAAAAAAAAAAAAAAAAMAQAAAQAYAAAQYAAAAAAAAAAAAAAAAAAiAQAAEgAOAFAGQAAAAAAAAgAAAAAAAAAyAQAAIAAAAAAAAAAAAAAAAAAAAAAAAACIAQAAIAAZAEAQYAAAAAAAAAAAAAAAAABOAQAAEgAAAAAAAAAAAAAAAAAAAAAAAABgAQAAEAAZAK0QYAAAAAAAAAAAAAAAAAAsAQAAEgAPAFQGQAAAAAAAAAAAAAAAAABnAQAAEgAAAAAAAAAAAAAAAAAAAAAAAACGAQAAEAAZAEAQYAAAAAAAAAAAAAAAAACTAQAAIAAAAAAAAAAAAAAAAAAAAAAAAACiAQAAEQIZAEgQYAAAAAAAAAAAAAAAAACvAQAAEQAQAGAGQAAAAAAABAAAAAAAAAC+AQAAEgAOAOAFQAAAAAAAZQAAAAAAAADYAAAAEAAaALAQYAAAAAAAAAAAAAAAAACMAQAAEgAOAHAEQAAAAAAAKgAAAAAAAADOAQAAEAAaAK0QYAAAAAAAAAAAAAAAAADaAQAAEgAOAGYFQAAAAAAAawAAAAAAAADfAQAAIAAAAAAAAAAAAAAAAAAAAAAAAADzAQAAEQIZALAQYAAAAAAAAAAAAAAAAAD/AQAAIAAAAAAAAAAAAAAAAAAAAAAAAAAZAgAAEgAAAAAAAAAAAAAAAAAAAAAAAADIAQAAEgALAAAEQAAAAAAAAAAAAAAAAAAAY3J0c3R1ZmYuYwBfX0pDUl9MSVNUX18AZGVyZWdpc3Rlcl90bV9jbG9uZXMAX19kb19nbG9iYWxfZHRvcnNfYXV4AGNvbXBsZXRlZC43NTk0AF9fZG9fZ2xvYmFsX2R0b3JzX2F1eF9maW5pX2FycmF5X2VudHJ5AGZyYW1lX2R1bW15AF9fZnJhbWVfZHVtbXlfaW5pdF9hcnJheV9lbnRyeQB0ZXN0LmMAbWFnaWMAX19GUkFNRV9FTkRfXwBfX0pDUl9FTkRfXwBfX2luaXRfYXJyYXlfZW5kAF9EWU5BTUlDAF9faW5pdF9hcnJheV9zdGFydABfX0dOVV9FSF9GUkFNRV9IRFIAX0dMT0JBTF9PRkZTRVRfVEFCTEVfAF9fbGliY19jc3VfZmluaQBfSVRNX2RlcmVnaXN0ZXJUTUNsb25lVGFibGUAcHV0c0BAR0xJQkNfMi4yLjUAX2VkYXRhAF9fbGliY19zdGFydF9tYWluQEBHTElCQ18yLjIuNQBfX2RhdGFfc3RhcnQAX19nbW9uX3N0YXJ0X18AX19kc29faGFuZGxlAF9JT19zdGRpbl91c2VkAF9fbGliY19jc3VfaW5pdABfX2Jzc19zdGFydABtYWluAF9Kdl9SZWdpc3RlckNsYXNzZXMAX19UTUNfRU5EX18AX0lUTV9yZWdpc3RlclRNQ2xvbmVUYWJsZQBzbGVlcEBAR0xJQkNfMi4yLjUAAC5zeW10YWIALnN0cnRhYgAuc2hzdHJ0YWIALmludGVycAAubm90ZS5BQkktdGFnAC5ub3RlLmdudS5idWlsZC1pZAAuZ251Lmhhc2gALmR5bnN5bQAuZHluc3RyAC5nbnUudmVyc2lvbgAuZ251LnZlcnNpb25fcgAucmVsYS5keW4ALnJlbGEucGx0AC5pbml0AC5wbHQuZ290AC50ZXh0AC5maW5pAC5yb2RhdGEALmVoX2ZyYW1lX2hkcgAuZWhfZnJhbWUALmluaXRfYXJyYXkALmZpbmlfYXJyYXkALmpjcgAuZHluYW1pYwAuZ290LnBsdAAuZGF0YQAuYnNzAC5jb21tZW50AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAbAAAAAQAAAAIAAAAAAAAAOAJAAAAAAAA4AgAAAAAAABwAAAAAAAAAAAAAAAAAAAABAAAAAAAAAAAAAAAAAAAAIwAAAAcAAAACAAAAAAAAAFQCQAAAAAAAVAIAAAAAAAAgAAAAAAAAAAAAAAAAAAAABAAAAAAAAAAAAAAAAAAAADEAAAAHAAAAAgAAAAAAAAB0AkAAAAAAAHQCAAAAAAAAJAAAAAAAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAABEAAAA9v//bwIAAAAAAAAAmAJAAAAAAACYAgAAAAAAABwAAAAAAAAABQAAAAAAAAAIAAAAAAAAAAAAAAAAAAAATgAAAAsAAAACAAAAAAAAALgCQAAAAAAAuAIAAAAAAAB4AAAAAAAAAAYAAAABAAAACAAAAAAAAAAYAAAAAAAAAFYAAAADAAAAAgAAAAAAAAAwA0AAAAAAADADAAAAAAAAQwAAAAAAAAAAAAAAAAAAAAEAAAAAAAAAAAAAAAAAAABeAAAA////bwIAAAAAAAAAdANAAAAAAAB0AwAAAAAAAAoAAAAAAAAABQAAAAAAAAACAAAAAAAAAAIAAAAAAAAAawAAAP7//28CAAAAAAAAAIADQAAAAAAAgAMAAAAAAAAgAAAAAAAAAAYAAAABAAAACAAAAAAAAAAAAAAAAAAAAHoAAAAEAAAAAgAAAAAAAACgA0AAAAAAAKADAAAAAAAAGAAAAAAAAAAFAAAAAAAAAAgAAAAAAAAAGAAAAAAAAACEAAAABAAAAEIAAAAAAAAAuANAAAAAAAC4AwAAAAAAAEgAAAAAAAAABQAAABgAAAAIAAAAAAAAABgAAAAAAAAAjgAAAAEAAAAGAAAAAAAAAAAEQAAAAAAAAAQAAAAAAAAaAAAAAAAAAAAAAAAAAAAABAAAAAAAAAAAAAAAAAAAAIkAAAABAAAABgAAAAAAAAAgBEAAAAAAACAEAAAAAAAAQAAAAAAAAAAAAAAAAAAAABAAAAAAAAAAEAAAAAAAAACUAAAAAQAAAAYAAAAAAAAAYARAAAAAAABgBAAAAAAAAAgAAAAAAAAAAAAAAAAAAAAIAAAAAAAAAAAAAAAAAAAAnQAAAAEAAAAGAAAAAAAAAHAEQAAAAAAAcAQAAAAAAADiAQAAAAAAAAAAAAAAAAAAEAAAAAAAAAAAAAAAAAAAAKMAAAABAAAABgAAAAAAAABUBkAAAAAAAFQGAAAAAAAACQAAAAAAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAACpAAAAAQAAAAIAAAAAAAAAYAZAAAAAAABgBgAAAAAAAHIAAAAAAAAAAAAAAAAAAAAIAAAAAAAAAAAAAAAAAAAAsQAAAAEAAAACAAAAAAAAANQGQAAAAAAA1AYAAAAAAAA0AAAAAAAAAAAAAAAAAAAABAAAAAAAAAAAAAAAAAAAAL8AAAABAAAAAgAAAAAAAAAIB0AAAAAAAAgHAAAAAAAA9AAAAAAAAAAAAAAAAAAAAAgAAAAAAAAAAAAAAAAAAADJAAAADgAAAAMAAAAAAAAAEA5gAAAAAAAQDgAAAAAAAAgAAAAAAAAAAAAAAAAAAAAIAAAAAAAAAAAAAAAAAAAA1QAAAA8AAAADAAAAAAAAABgOYAAAAAAAGA4AAAAAAAAIAAAAAAAAAAAAAAAAAAAACAAAAAAAAAAAAAAAAAAAAOEAAAABAAAAAwAAAAAAAAAgDmAAAAAAACAOAAAAAAAACAAAAAAAAAAAAAAAAAAAAAgAAAAAAAAAAAAAAAAAAADmAAAABgAAAAMAAAAAAAAAKA5gAAAAAAAoDgAAAAAAANABAAAAAAAABgAAAAAAAAAIAAAAAAAAABAAAAAAAAAAmAAAAAEAAAADAAAAAAAAAPgPYAAAAAAA+A8AAAAAAAAIAAAAAAAAAAAAAAAAAAAACAAAAAAAAAAIAAAAAAAAAO8AAAABAAAAAwAAAAAAAAAAEGAAAAAAAAAQAAAAAAAAMAAAAAAAAAAAAAAAAAAAAAgAAAAAAAAACAAAAAAAAAD4AAAAAQAAAAMAAAAAAAAAQBBgAAAAAABAEAAAAAAAAG0AAAAAAAAAAAAAAAAAAAAgAAAAAAAAAAAAAAAAAAAA/gAAAAgAAAADAAAAAAAAAK0QYAAAAAAArRAAAAAAAAADAAAAAAAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAMBAAABAAAAMAAAAAAAAAAAAAAAAAAAAK0QAAAAAAAANQAAAAAAAAAAAAAAAAAAAAEAAAAAAAAAAQAAAAAAAAARAAAAAwAAAAAAAAAAAAAAAAAAAAAAAACMGQAAAAAAAAwBAAAAAAAAAAAAAAAAAAABAAAAAAAAAAAAAAAAAAAAAQAAAAIAAAAAAAAAAAAAAAAAAAAAAAAA6BAAAAAAAAB4BgAAAAAAAB4AAAAwAAAACAAAAAAAAAAYAAAAAAAAAAkAAAADAAAAAAAAAAAAAAAAAAAAAAAAAGAXAAAAAAAALAIAAAAAAAAAAAAAAAAAAAEAAAAAAAAAAAAAAAAAAAA=')
with open('test1','wb')as f:
f.write(data)
./test1
hei~what you want??
want a flag?
sorry~there is no flag
but maybe your can find something useful!然后分析wav ,sileneye
第三个文件夹打开
1. 加入代码隐写的部分不能影响源代码的编译
2. 不能很容易被公司审计专员看出来
3. 不能直接明文交流
md写了不能明文交流,联想到tab和空格,但是几千个文件,挨个查看不现实,因此考虑写个脚本搜索,由于tab和空格编写的隐藏数据通常是连续的,同时要过滤到常见的双空格和双/t,因此考虑用 \t \t作为搜索字符
import os
def get_file_list(dir_path):
_list = os.listdir(dir_path)
file_list = []
for file_str in _list :
new_dir_path = dir_path+ '\\' +file_str
if os.path.isdir(new_dir_path):
file_list.extend(get_file_list(new_dir_path))
else :
file_list.append(new_dir_path)
return file_list
file_list = get_file_list(r'c:\Users\86157\Desktop\新建文件夹2\buu\attachment2\日记3\文件夹')
for file_str in file_list :
f = open(file_str,'r',encoding = 'utf-8')
try:
data = f.read()
if ' \t \t' in data :
print(file_str)
except :
pass打开后发现每个} 后面 有隐写
f_list = r'''c:\Users\86157\Desktop\新建文件夹2\buu\attachment2\日记3\文件夹\elf\rtld.c
c:\Users\86157\Desktop\新建文件夹2\buu\attachment2\日记3\文件夹\malloc\arena.c
c:\Users\86157\Desktop\新建文件夹2\buu\attachment2\日记3\文件夹\malloc\malloc.c'''
f_list = f_list.split('\n')
result = ''
for f in f_list:
for data in open(f, 'r').readlines():
data = data[:-1]
if '}' in data:
data = data.split('}')[-1]
if '\t' in data:
data1 = data[::].replace('\t', '')
data1 = data1.replace(' ', '')
if not data1:
result += data
result = result.replace('\t', '1')
result = result.replace(' ', '0')
print(result)
得到
01010011010011110101001100100001001000000111000001101100011001010110000101110011011001010010000001101000011001010110110001110000001000000110110101100101001000000010110100111110001000000111001001110100011011000110010000101110011000110111100101101111011101010111001000100000011001100110110001100001011001110010000001101001011100110010000001101001011011100010000001101101011000010110110001101100011011110110001100101110011000110100011101010111010000110101010001000110011110110110001101101111011001000110010101011111011100110111010001100101011001110110000101101110011011110110011101110010011000010111000001101000011110010101111100110001011100110101111101100110011101010110111001101110011110010010000101111101转ascii
SOS! please help me -> rtld.cyour flag is in malloc.cGWCTF{code_steganography_1s_funny!}




